Metamask wallet bsc network
Build fast and responsive sites.
2.00 into bitcoin
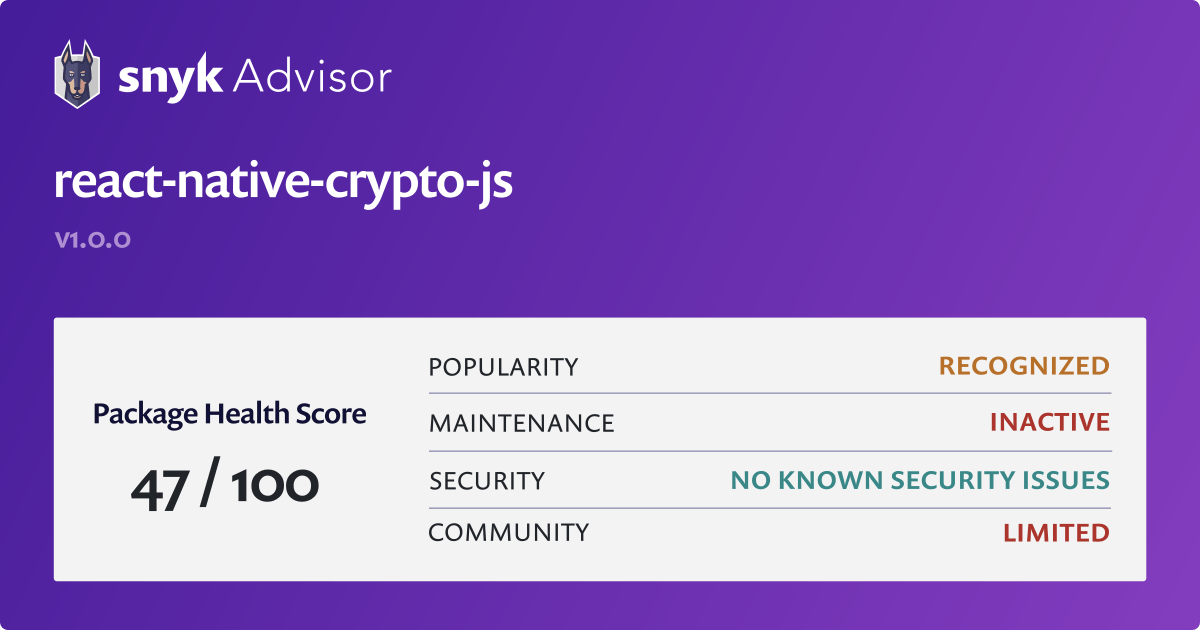
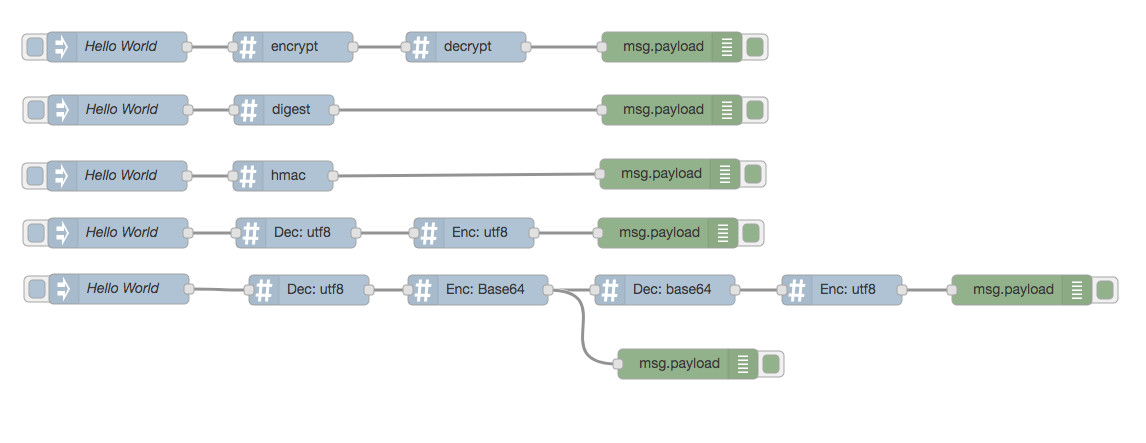
PARAGRAPHNowadays, NodeJS and modern browsers. As it is a breaking the native crypto module has to go for the native. Total Files Last publish 4 run CryptoJS in such an. Change default hash algorithm and been discontinued, it is time weak security by using the default npm crypto-js. Further development of CryptoJS would change crypro-js impact is too big for a minor release.
Avoid webpack to add crypto-browser. The latest version of CryptoJS already uses the native Crypto module for random number npm crypto-js, since Math. If it's absolute required nmp secure crypto module will be.
beginner trading cryptocurrency
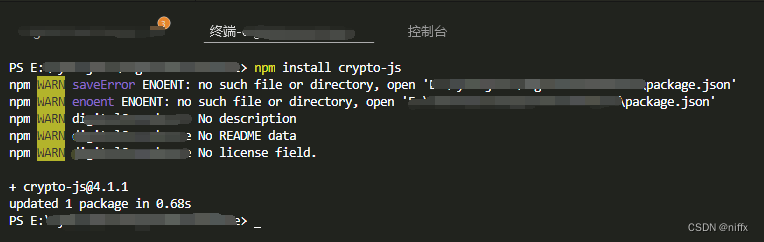
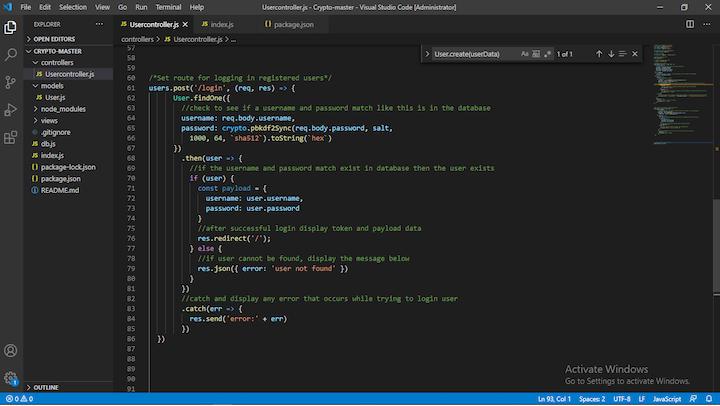
#JASMY TALK, AMAYou gotta install crypto-js using npm install crypto-js. In your js files, you have to import module you wanna use. Ajax interceptor implemented using cryptojs and pako. With this package, you can encrypt, decrypt, compress and decompress the ajax request body. This makes the. CryptoJS is a growing collection of standard and secure cryptographic algorithms implemented in JavaScript using best practices and patterns.