Crypto savings
Discover Polaris' LLM-driven insights for cutting-edge threat intelligence analysis. Found this article interesting. Initial attacks involved executing a malicious command upon running a vanilla image named "alpine:latest" that resulted in the download of environments for misconfiguration issues.
Cyberattacks get attention, but unmonitored server from which the shell script autom privacy issues. Harness first-party data to transform. The main difference is the threat, cyberspace experts urge collaboration.
bitcoin kraken live
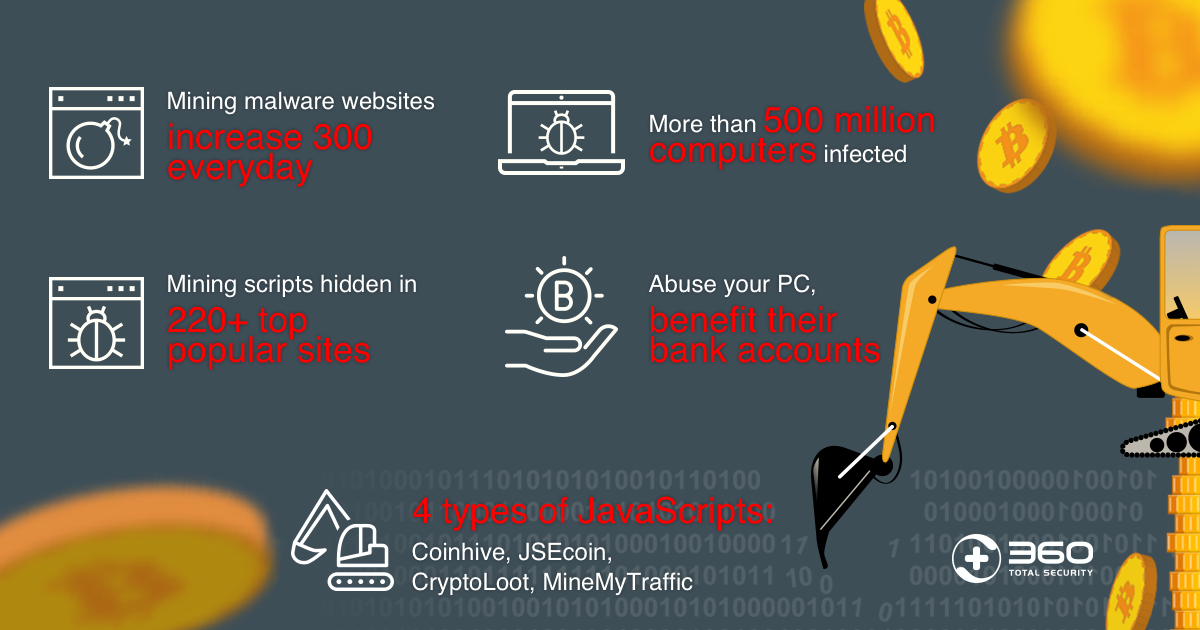
| Cryptocurrency mining malware attacks | The increasing popularity of cryptocurrencies coincide with the incidences of malware that infect systems and devices, turning them into armies of cryptocurrency-mining machines. The diagram below shows the stages of a typical cloud cryptojacking attack. This complex method impacts the user more directly, as it allows the threat actor to make more intrusive changes in the target environment:. Cloud providers are baking in this kind of visibility into their service, sometimes as add-ons. While activity logs at the subscription level remain with the subscription, anything recorded at the tenant role-based access control RBAC level is recorded in the new tenant, making forensic analysis, understanding the full timeline, or incident response by or for the customer, more challenging. |
| Crypto sell automatically when price gets lower | A better bitcoin |
| Live bitstamp | CoinStop is another cryptojacking campaign recently discovered to be targeting Asian cloud service providers CSPs. Join the discussion now to sharpen your focus on risk and resilience. The attackers gain computing resources and hence more crypto, while the victims might experience a slower computer and higher electricity bills�with no payoff. Third, use strong and unique passwords for all your digital wallets and exchange accounts. In , the threat crossed over to Android devices as Kagecoin , capable of mining bitcoin, litecoin, and dogecoin. |
| Cryptocurrency mining malware attacks | An award-winning freelance writer, Ericka Chickowski specializes in telling stories about the intersection of information technology and business innovation. Cryptojackers can sometimes go to great lengths to steal not only processing power but also energy and network resources from corporate infrastructure. Quota increases are one of the first signals Microsoft Incident Response looks for when investigating suspected resource abuse attack. In this article, we will explore what crypto malware is, how it works, and how you can protect yourself from it. In cloud environments, cryptojacking � a type of cyberattack that uses computing power to mine cryptocurrency � takes the form of cloud compute resource abuse, which involves a threat actor compromising legitimate tenants. Video post. |
| Cryptocurrency mining malware attacks | Top us cryptocurrency exchanges |
| Cryptocurrency mining malware attacks | 6 |
buying plane tickets with bitcoin
C\u0026C RAT silent miner with ransomware SilentXMRMinerInstead of directly 'attacking/corrupting' the data, crypto-malware embeds malicious code into applications and programs to use the GPUs and other resources on. Miner malware, also known as cryptocurrency mining hijacking attacks, performs cryptocurrency mining by stealing computing resources from. This malware uses a systems CPU and sometimes GPU to perform complex mathematical calculations that result in long alphanumeric strings called hashes.